Deep Dive into SnakeKeylogger Malware

Snake Keylogger is a relatively new credential stealer and keylogger, first detected in the wild in November 2020. Written in .NET, this modular malware is equipped with several malicious capabilities, including keylogging, stealing saved credentials, capturing screenshots, and harvesting clipboard data to send to the attacker.
Snake Keylogger is typically distributed through phishing and spear-phishing campaigns, where a malicious Office document or PDF is attached to the email. If the recipient opens the document and enables macros, or if they are using a vulnerable version of Office the malware is executed. The malware embedded in the document often acts as a downloader, utilizing PowerShell scripts to fetch and execute a copy of Snake-Keylogger on the infected system. Snake-Keylogger represents a serious threat to both corporate and personal cybersecurity.
Infection Chain:
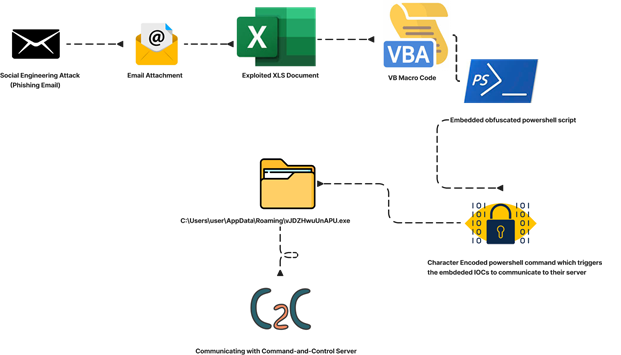
Snake Keylogger gains access via phishing emails or compromised sites, setting up a stronghold and linking to a remote server. In general, by using encrypted channels, it extracts data and executes remote operations, potentially launching more assaults. To evade detection, it employs evasion tactics, demanding a comprehensive defense strategy involving updated tools, vigilant network oversight, user awareness, and timely security patches.
Technical Analysis of Snake Keylogger Malware:
Malware creators often choose XLS documents to deceive people into opening them. Since XLS files are commonly used and generally considered safe, they tend to be trusted by users. However, attackers exploit vulnerabilities in these documents to insert malicious content.
By disguising the files as legitimate communications from trusted companies or individuals, attackers can easily trick users. The widespread compatibility of XLS files across various devices makes it easier for attackers to target a larger audience. Additionally, malicious content can be hidden within the file itself, making it more difficult for security tools to detect. As a result, these harmful files often go unnoticed and can cause significant damage once opened, making XLS files a preferred vehicle for initiating cyber attacks.
Manual Extraction of XLS:
Let’s examine the XLS file using manual extraction. Once extracted, we can see the embedded files. In this case, we found three different folders, each with randomized names. Let’s delve into those folders to investigate further.
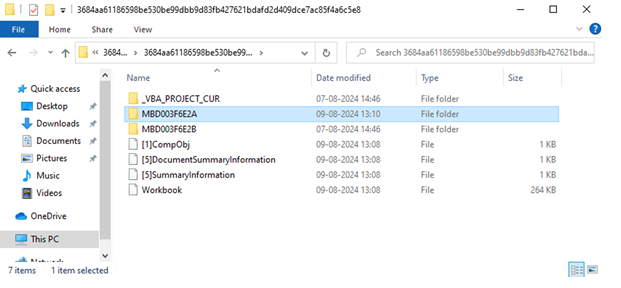
Package Folder:
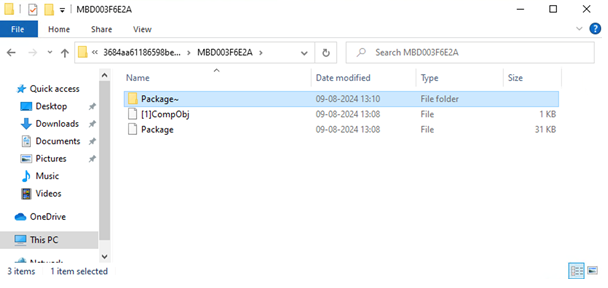
Embedded XLS Document:
After extracting multiple folders, we discovered another embedded XLS document, which contains an additional payload file.
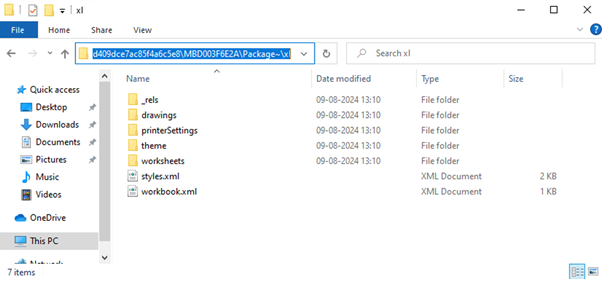
Dynamic Inspection of XLS:
Based on our static inspection, we've gathered valuable insights. Now, we'll proceed with the dynamic analysis to further investigate the behavior of the file in a live environment.
Sheet2:
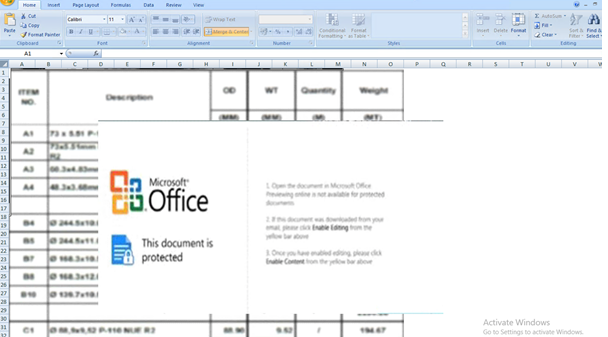
Sheet3:
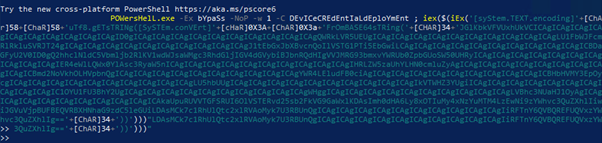
Obtained Powershell Command:
Obtained URL:
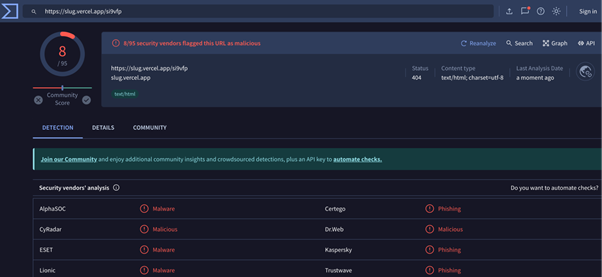
The submitted URLs domain IP has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.
Recommendations:
Here are simplified recommendations for dealing with Pikabot Malware.
- Apply the Microsoft-provided security patch to resolve the vulnerability.
- Educate your users to identify and steer clear of suspicious email attachments.
- Deploy email filters to block or isolate malicious attachments.
- Ensure your antivirus software is current to detect and thwart malware.
- Regularly backup vital data and have a recovery strategy in place for potential attacks.
Advisory & Compliance Services
Audit & Assessment Services
Managed Security Services
Governance & Compliance Framework Development
Cyber Key Performance IndicatorsCISO Advisory
Advisory and Compliance ServicesStandard & Regulatory AdvisoryBusiness Continuity & Disaster Recovery PlanningIncident Response ReadinessData Privacy
Audit and Assessment Services
Cloud Security Assessment
Cyber Maturity Assessment
Privacy Impact Assessment
Red Teaming Service
VAPT
Managed Security Services
SOC as a Service
Third Party Risk Management
Vulnerability Management Services