Deep Diving into XenoRAT Malware Campaign

XenoRAT is a remote access trojan (RAT) that is open-source and written in C#, making it freely accessible on platforms like GitHub. Although it was initially created for educational purposes, it has been widely adopted by malicious actors for nefarious activities. This malware primarily targets Windows systems, enabling attackers to remotely control infected devices.
XenoRAT’s capabilities include logging keystrokes, manipulating files, installing and uninstalling software, and executing commands. It is known for its advanced evasion techniques, such as obfuscation to hide its presence, process injection to run within legitimate processes, and the use of SOCKS5 proxies for secure command-and-control (C2) server communication.
How does it spread?
The malware is distributed through various methods, including phishing emails and drive-by downloads, often disguising itself as legitimate applications like video game installers. It can monitor user activities covertly using hidden virtual network computing (VNC) and maintain persistence on infected systems via scheduled tasks. Additionally, it can uninstall itself to avoid detection.
XenoRAT’s continuous updates and sophisticated techniques make it a significant threat to individuals and organizations, allowing attackers to exfiltrate data and maintain long-term control over compromised systems.
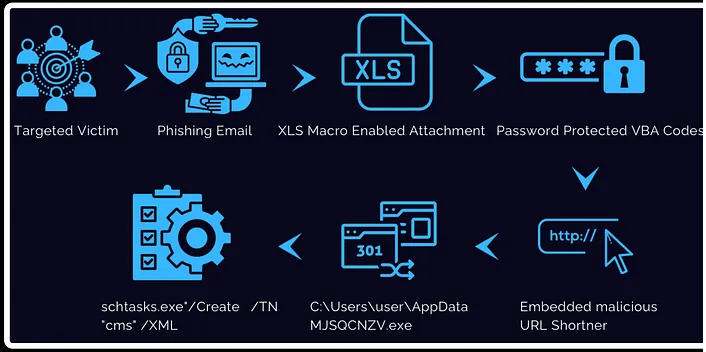
Infection Chain
Malware authors often use Excel (.XLS or .XLSX) files as an initial vector for several reasons:
User Trust: Excel files are commonly used and trusted in businesses, making people more likely to open them, especially if they appear to come from a known source.
Macro Functionality: Excel files can contain macros, which can execute malicious code when enabled, allowing for the automation of harmful activities on the victim’s computer.
Evasion Techniques: Malware authors use obfuscation in macros to avoid detection by antivirus software, making it easier for the malicious code to bypass security measures.
Social Engineering: Attackers craft convincing phishing emails to trick recipients into opening Excel files and enabling macros, leveraging human error and curiosity.
Wide Compatibility: Excel files can be opened on various systems and software versions, increasing the likelihood of a successful attack and making them easy to distribute via email or downloads.
Technical Analysis of XenoRAT Malware Using .XLS:
Download the malware sample in a secure testing environment. When analyzing any file, extract it to identify suspicious elements or URLs. In this case, we are examining an XLS file, which is a compound object file, allowing us to extract and inspect its binaries and embedded files.
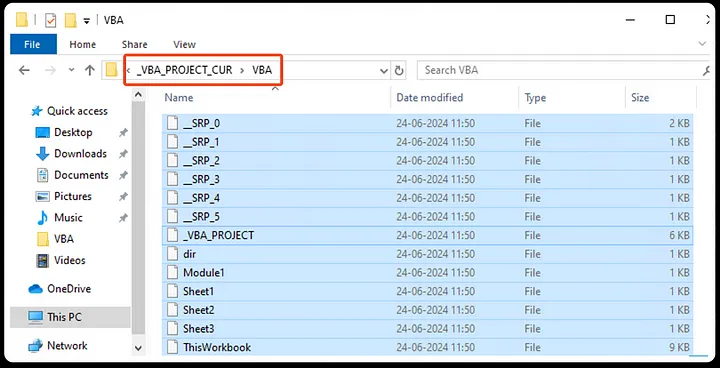
Extracted XLS file
Dynamic Inspection:
Dynamic analysis helps us to directly observe how malware behaves during execution. This encompasses monitoring file system alterations, network interactions, registry adjustments, and engagements with system processes. Such observations are crucial for deciphering the malware’s objectives and functionalities.
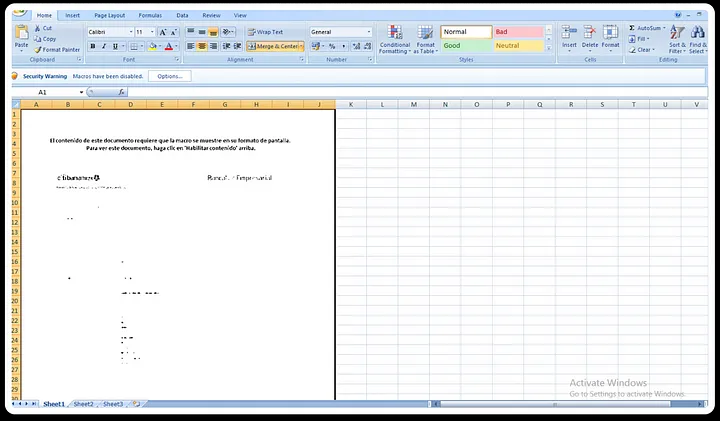
XenoRAT XLS Template
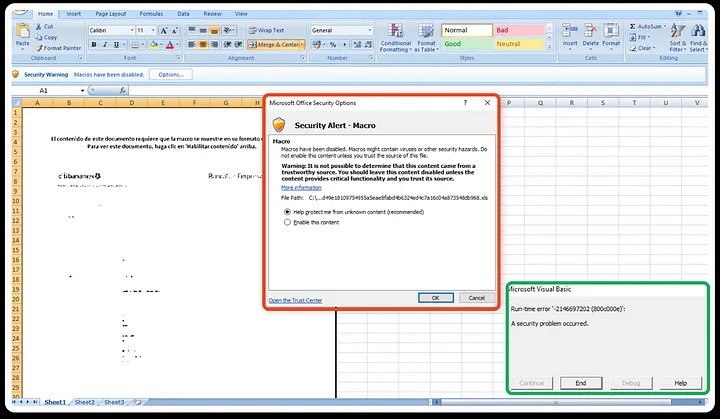
VBA Macro Enabled
Upon opening the XLS sheet, it will initially display a blurred image. Above it, a message will indicate that macros are disabled and prompt to enable them to view the content. Once macros are enabled, the embedded malicious URL attempts to connect to the network and download a payload file into the %appdata% directory, subsequently executing malicious operations.
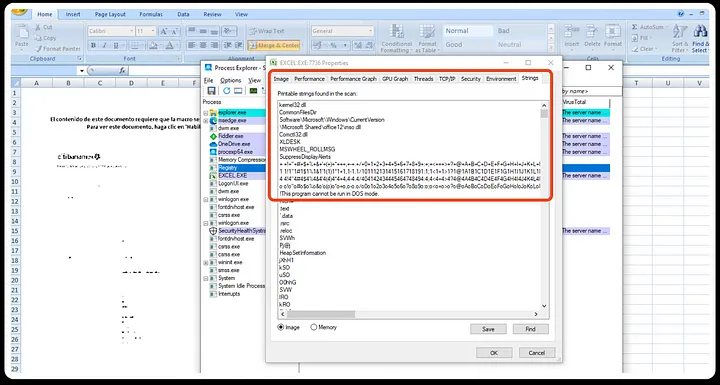
Password Protected XLS Module
The sample obtained has its macro modules protected with a password in Sheet1, while Sheet2 and Sheet3 are empty.
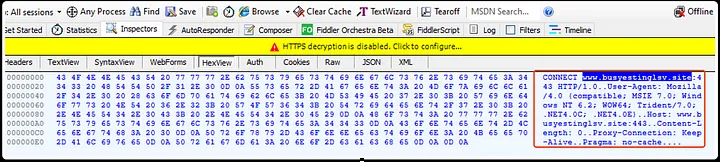
HTTP Packet Capture
Obtained IOC Sandbox Results:
Indicators of Compromise (IoCs) are signs or clues that suggest a computer system has been breached or compromised, helping cybersecurity experts detect and respond to security incidents. They include abnormal activities, patterns, or artifacts that may indicate unauthorized access or malicious actions.
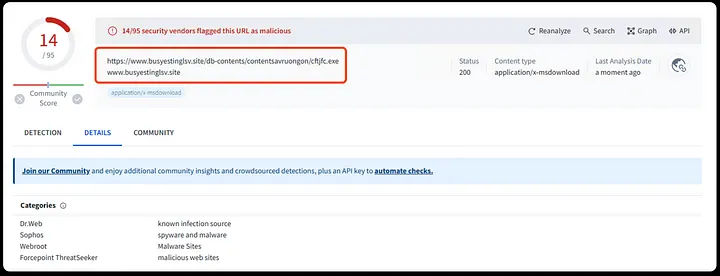
AV Sandbox Results
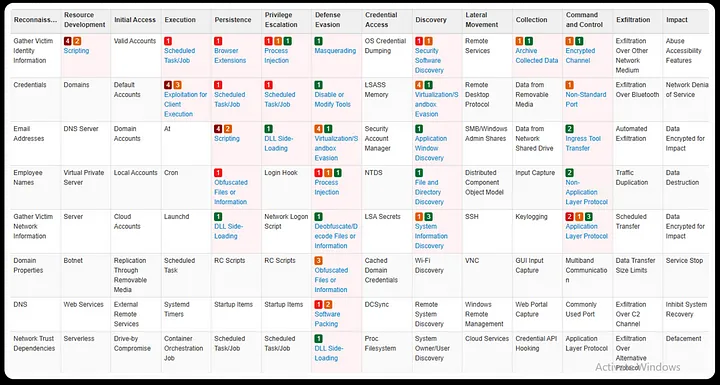
MITRE ATT&CK Framework
Advisory & Compliance Services
Audit & Assessment Services
Managed Security Services
Governance & Compliance Framework Development
Cyber Key Performance IndicatorsCISO Advisory
Advisory and Compliance ServicesStandard & Regulatory AdvisoryBusiness Continuity & Disaster Recovery PlanningIncident Response ReadinessData Privacy
Audit and Assessment Services
Cloud Security Assessment
Cyber Maturity Assessment
Privacy Impact Assessment
Red Teaming Service
VAPT
Managed Security Services
SOC as a Service
Third Party Risk Management
Vulnerability Management Services