OTP Bypass via Response Manipulation

One-Time Passwords (OTPs) are widely used as a security measure for authenticating users, offering an additional layer of protection against unauthorized access. However, vulnerabilities like OTP bypass via response manipulation can significantly weaken the effectiveness of this multi-factor authentication method.
The response manipulation technique allows attackers to gain unauthorized access by intercepting and altering the server's response during the OTP verification process. The root cause lies in weak server-side validation, where applications rely on the client’s response instead of re-checking the OTP on the server. This trust in client-side responses, coupled with the absence of integrity checks, creates an exploitable gap in security.
In this blog, let’s explore this vulnerability in depth through real-world examples and case studies. Further, let’s know the proven methods to secure servers and communication protocols effectively.
Understanding OTP Bypass via Response Manipulation
Response manipulation occurs when an attacker intercepts and modifies the server’s response to achieve unauthorized access. Many applications rely on an API that verifies the OTP and returns a success or failure response. If this response is not properly secured, it can be altered to grant unauthorized access.

How OTP Bypass via Response Manipulation Works
Many web applications communicate with backend servers via API calls. When a user enters an OTP, the application sends a request to the server, which verifies the OTP and returns a response. If this response is not properly secured, an attacker can manipulate it to bypass authentication.
Here’s how it works in theory:
1. Weak Server-Side Validation: If the backend server only relies on client-side confirmation rather than rechecking the OTP on the server side, it becomes vulnerable.
2. Modifiable Response Data: The server sends a response containing flags such as `isVerified: false` or `status: failure`, which attackers can modify.
3. Client-Side Trust Issues: If the application trusts manipulated responses without revalidating them on the backend, an attacker can gain unauthorized access.
Real-World Example
Consider an online service where users enter an OTP sent via SMS. The OTP verification request might look like this:

If the response from the server is: false

An attacker can modify this response to: true

If the application does not revalidate the OTP on the server side, unauthorized access is granted.
Case Study: OTP Bypass on Restaurant ‘XYZ’
[Restaurant ‘XYZ’: The client's identity remains confidential in accordance with our commitment to privacy and discretion.]
During security research, we examined the registration process on XYZ’ s restaurant onboarding portal. Below is the step-by-step approach taken to identify the OTP bypass vulnerability.
Submitting Business Details: Enter a business name, email, and phone number, then click on “Verify” to receive an OTP.
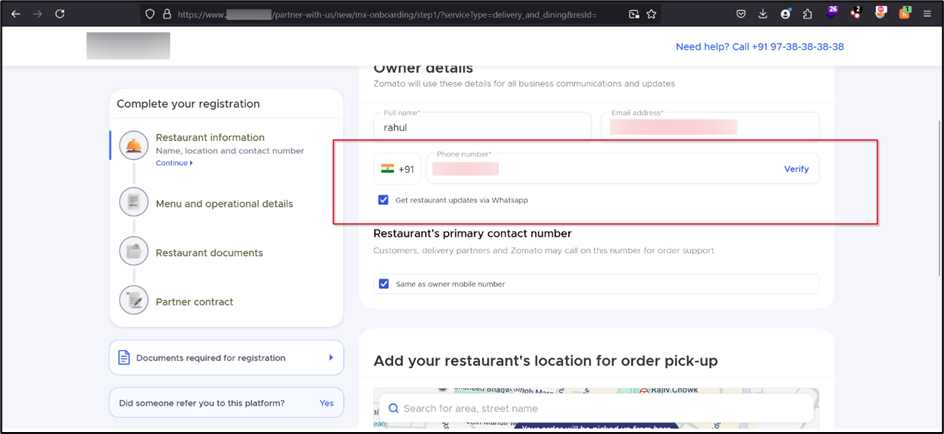
Testing with an Invalid OTP: Enter an incorrect OTP (e.g., 123456). The system displays an error message stating that the OTP is invalid.

Intercepting the HTTP Request: intercept the request when the OTP is submitted. The response from the server contains a verification status field.
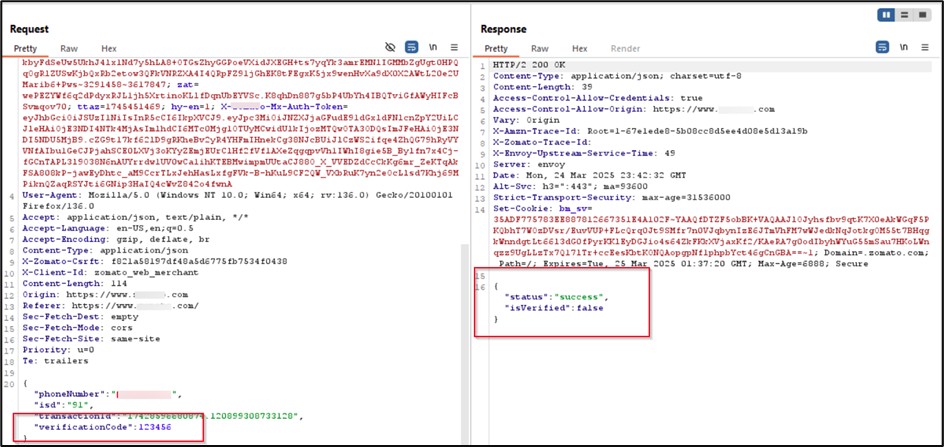
Modifying the Server Response: Change the field "isVerified": false to "isVerified": true in the response. This modification allows the registration process to be completed successfully without entering a valid OTP.


Root Cause of the Vulnerability
The primary reason for this OTP bypass vulnerability is the lack of proper server-side validation. Instead of enforcing OTP verification on the backend, the system relies on the response from the client-side, which can be easily intercepted and manipulated. Other contributing factors include:
- Client-Side Trust: The application trusts client-side responses without verifying them on the server.
- Lack of Request Integrity Checks: No cryptographic methods (e.g., HMAC validation) are used to ensure the request's authenticity.
Responsible Disclosure
This vulnerability was reported to HackerOne through a Bug Bounty program. The affected platform was notified.
Prevention Measures
1. Server-Side Validation: Always handle OTP verification on the server to maintain control and security. Client-side validation, such as JavaScript checks, can be bypassed by attackers using browser tools, proxy interceptors like Burp Suite. Server-side verification ensures that the OTP is validated against a secure, trusted source (like a database or cache), with proper checks for expiration, single-use validity, and user association. This approach prevents unauthorized access even if the client app is compromised.
2. Token-Based Authentication: Using encrypted, time-bound tokens instead of plain OTPs increases the security and flexibility of your authentication system. Tokens like JWT (JSON Web Token) can carry user-specific claims and expiration times, and they are signed to prevent tampering. This means even if someone intercepts the token, they can't modify or reuse it. Tokens also make session handling easier in stateless applications like REST APIs and reduce reliance on traditional session storage, while providing enhanced control over token lifespan and scope.
3. Implement Rate Limiting: Rate limiting helps defend against brute-force and enumeration attacks by restricting the number of OTP attempts allowed within a certain time period per user, IP, or device. Without it, attackers could script multiple attempts to guess the correct OTP. Implementing mechanisms like per-minute limits, exponential backoff, or temporary user lockouts after repeated failures significantly increases security. It also helps detect abnormal behavior and can trigger alerts for suspicious activity, contributing to better incident response.
4. System-Level Measures: Maintain logs and actively monitor OTP usage for unusual patterns or repeated failures. Introduce CAPTCHAs to ensure that OTP requests come from legitimate users rather than bots. Modern CAPTCHAs, such as reCAPTCHA, employ advanced algorithms to differentiate between humans and bots while maintaining a seamless user experience. These CAPTCHAs can be implemented dynamically, triggered only after unusual activity, such as a high volume of OTP requests or suspected bot behavior.
The Role of User Awareness
While server-side measures are paramount, educating users about secure OTP practices is equally important. Users should:
- Avoid sharing OTPs with anyone.
- Recognize phishing attempts aimed at collecting OTPs.
- Use applications that prioritize robust OTP mechanisms.
Conclusion
OTP bypass via response manipulation is a severe security risk that can compromise user accounts. Relying on client-side responses without proper revalidation creates exploitable vulnerabilities that attackers can easily target. Developers must implement strong server-side validation, secure API communications, encrypted token-based authentication, and monitor for anomalies to prevent exploitation. Adopting these best security practices enables businesses to protect their users from unauthorized access and maintain trust in their applications.
Advisory & Compliance Services
Audit & Assessment Services
Managed Security Services
Governance & Compliance Framework Development
Cyber Key Performance IndicatorsCISO Advisory
Advisory and Compliance ServicesStandard & Regulatory AdvisoryBusiness Continuity & Disaster Recovery PlanningIncident Response ReadinessData Privacy
Audit and Assessment Services
Cloud Security Assessment
Cyber Maturity Assessment
Privacy Impact Assessment
Red Teaming Service
VAPT
Managed Security Services
SOC as a Service
Third Party Risk Management
Vulnerability Management Services